Which of the following tasks fall under the responsibility of the SSL proxy in a typical HTTPS connection? (Select all that apply.)
A. The web server SSL handshake.
B. The web client SSL handshake.
C. File buffering.
D. Communication with the urlfilter process.
正解:A,B
質問 2:
Review the output of the command get router info routing-table database shown in the Exhibit below; then answer the question following it.
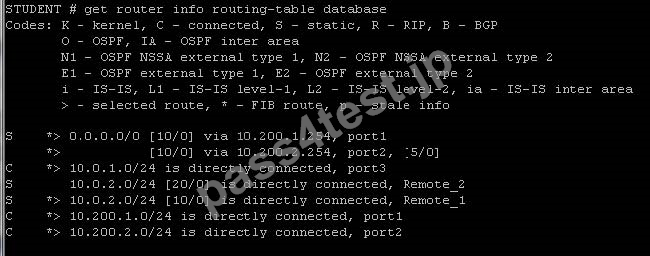
Which of the following statements are correct regarding this output? (Select all that apply).
A. There will be two routes for the 10.0.2.0/24 subnet in the routing table.
B. There will be two default routes in the routing table.
C. There will be six routes in the routing table.
D. There will be seven routes in the routing table.
正解:B,C
質問 3:
The following diagnostic output is displayed in the CLI:
diag firewall auth list
policy iD. 9, srC. 192.168.3.168, action: accept, timeout: 13427
user: forticlient_chk_only, group:
flag (80020): auth timeout_ext, flag2 (40): exact group iD. 0, av group: 0
----- 1 listed, 0 filtered -----
Based on this output, which of the following statements is correct?
A. This user has been associated with a guest profile as evidenced by the group id of 0.
B. Firewall policy 9 has endpoint compliance enabled but not firewall authentication.
C. The client check that is part of an SSL VPN connection attempt failed.
D. An auth-keepalive value has been enabled.
正解:B
質問 4:
Which of the following statements is correct regarding the FortiGuard Services Web Filtering Override configuration as illustrated in the exhibit?

A. A client with an IP of address 10.10.10.12 is allowed access to any subdirectory that is part of the www.yahoo.com web site.
B. A client with an IP address of 10.10.10.12 is allowed access to the www.yahoo.com/images/ web site and any of its offsite URLs.
C. Any client on the same subnet as the authenticated user is allowed to access www.yahoo.com/images/ until August 7, 2009.
D. Any client on the same subnet as the authenticated user is allowed to access www.yahoo.com/images/.
E. A client with an IP address of 10.10.10.12 is allowed access to any URL under the www.yahoo.com web site, including any subdirectory URLs, until August 7, 2009.
正解:B
質問 5:
Shown below is a section of output from the debug command diag ip arp list.
index=2 ifname=port1 172.20.187.150 00:09:0f:69:03:7e state=00000004 use=4589 confirm=4589 update=2422 ref=1
In the output provided, which of the following best describes the IP address 172.20.187.150?
A. It is the IP address of another network device located in the same LAN segment as the FortiGate unit's port1 interface.
B. It is the primary IP address of the port1 interface.
C. It is one of the secondary IP addresses of the port1 interface.
正解:A
質問 6:
Which of the following report templates must be used when scheduling report generation?
A. Data Filter Template
B. Chart Template
C. Layout Template
D. Output Template
正解:C
質問 7:
The eicar test virus is put into a zip archive, which is given the password of "Fortinet" in order to open the archive. Review the configuration in the exhibits shown below; then answer the question that follows.
Exhibit A - Antivirus Profile:
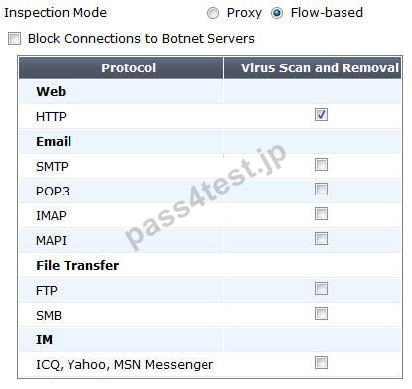
Exhibit B - Non-default UTM Proxy Options Profile: Exhibit C - DLP Profile:
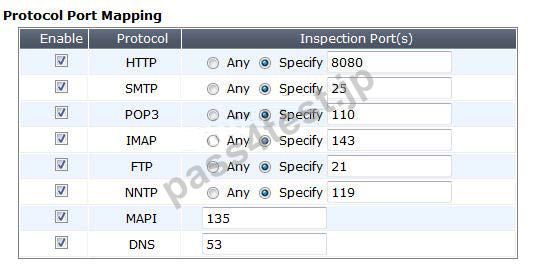
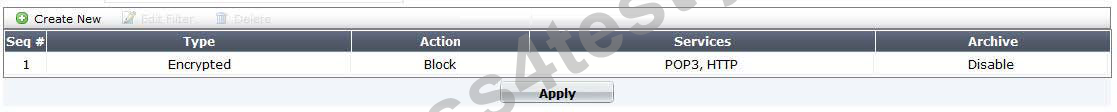
Which of one the following profiles could be enabled in order to prevent the file from passing through the FortiGate device over HTTP on the standard port for that protocol?
A. Only Exhibit A
B. Only Exhibit C with default UTM Proxy settings.
C. Only Exhibit C with non-default UTM Proxy settings (Exhibit B).
D. All of the Exhibits (A, B and C)
E. Only Exhibit B
正解:B
質問 8:
In a High Availability configuration operating in Active-Active mode, which of the following correctly describes the path taken by a load-balanced HTTP session?
A. Request: Internal Host -> Master FG -> Slave FG -> Master FG -> Internet -> Web Server
B. Request: Internal Host -> Slave FG -> Internet -> Web Server
C. Request: Internal Host -> Master FG -> Slave FG -> Internet -> Web Server
D. Request: Internal Host -> Slave FG -> Master FG -> Internet -> Web Server
正解:C
質問 9:
WAN optimization is configured in Active/Passive mode. When will the remote peer accept an attempt to initiate a tunnel?
A. The attempt will be accepted when there is a matching WAN optimization passive rule.
B. The attempt will be accepted when a user on the remote peer accepts the connection request.
C. The attempt will be accepted when the request comes from a known peer.
D. The attempt will be accepted when the request comes from a known peer and there is a matching WAN optimization passive rule.
正解:D


 814 お客様のコメント
814 お客様のコメント クリック」
クリック」






荻野** -
短時間で勉強になりました。そして試験にも無事合格です!無事、試験に合格することができました。Pass4Testさん、やはり信頼できますね。