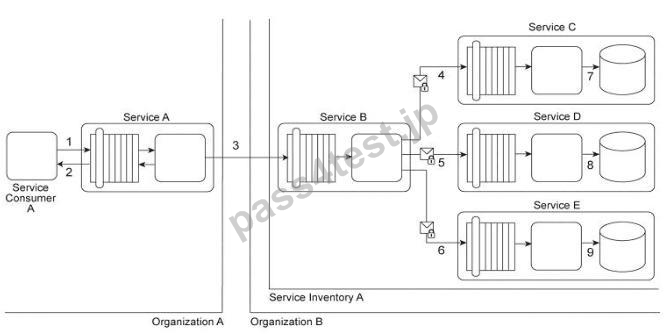
Service A provides a data retrieval capability that can be used by a range of service consumers, including Service Consumer A, In order to retrieve the necessary data. Service Consumer A first sends a request message to Service A (1). Service A then exchanges request and response messages with Service B (2, 3). Service C (4, 5), and Service D (6.
7). After receiving all three response messages from Services B.
C. and D, Service A assembles the collected data into a response message that it returns to Service Consumer A (8).
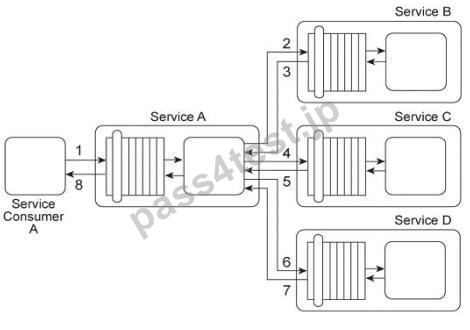
The Service A data retrieval capability has been suffering from poor performance, which has reduced its usefulness to Service Consumer A.
Upon studying the service composition architecture, it is determined that the performance problem can be partially attributed to redundant validation by service contracts for compliance to security policies. Services B and C have service contracts that contain the same two security policies. And, Service D has a service contract that contains a security policy that is also part of Service A's service contract.
What changes can be made to the service contracts in order to improve the performance of the service composition while preserving the security policy compliance requirements?
A. Apply the Standardized Service Contract principle in order to remove redundancy within service contracts by ensuring that all four service contracts comply with the same policy standards. This further requires the application of the Service Abstraction principle to guarantee that policy definitions are sufficiently streamlined for performance reasons.
B. Apply the Policy Centralization pattern in order to establish two centralized policy definitions and ensure that policy enforcement logic is correspondingly centralized. The first policy definition includes the redundant security policies from Services A and D and the second policy definition contains the redundant security policies from Services B and C.
C. All policies are analyzed for similarities, which are then extracted and, by applying the Policy Centralization pattern, combined into a single policy definition. This "meta-policy" is then positioned to perform validation of the response message generated by Service A, prior to receipt by Service Consumer A.
If validation fails, an alternative error message is sent to Service Consumer A instead.
D. Apply the Policy Centralization pattern in order to establish a single security policy for the entire service composition. The redundant policies residing in the service contracts of Services A.
B, C and D need to be removed and grouped together into one master policy definition enforced by Service A.
This way, redundant policy validation is eliminated, thereby improving runtime performance.
正解:B
質問 2:
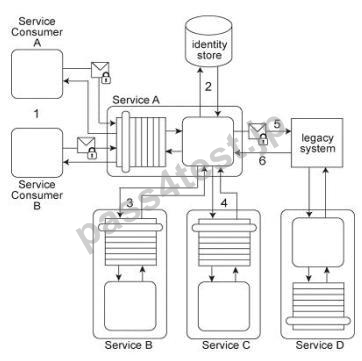
Service A provides a customized report generating capability. Due to infrastructure limitations, the number of service consumers permitted to access Service A concurrently is strictly controlled. Service A validates request messages based on the supplied credentials (1). If the authentication of the request message is successful, Service A sends a message to Service B (2) to retrieve the required data from Database A (3). Service A stores the response from Service B (4) in memory and then issues a request message to Service C (5). Service C retrieves a different set of data from Database A (6) and sends the result back to Service A (7). Service A consolidates the data received from Services B and C and sends the generated report in the response message to the service consumer (8).
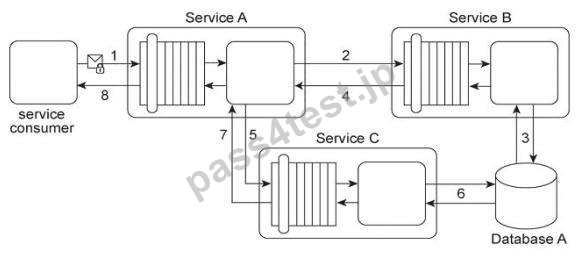
It has been discovered that attackers have been gaining access to confidential data exchanged between Service A and Service B, and between Service A and its service consumers. What changes can be made to this service composition architecture in order to counter this threat?
A. Apply the Direct Authentication pattern in order to protect message exchanges between Service A and its service consumers and between Service A and Service B.
This approach will establish a password-based authentication mechanism that relies on a local identity store and will therefore prevent access by attackers.
B. Apply the Data Origin Authentication pattern to protect the final report sent by Service A to its service consumer. Service A can generate a message digest of the final report, after which it can sign the digest with its own private key. It then can send both the final report and the signed message digest to its service consumer. This service consumer can generate its own message digest, decrypt the signed digest using the public key of Service A (which proves that Service A sent the message), and then compare the two digests. If the digests match, it guarantees that the final report was not tampered with during transmission.
C. Apply the Service Perimeter Guard pattern in order to protect message exchanges between Service A and its service consumers. Apply the Direct Authentication pattern in order to protect message exchanges between Service A and Service B.
D. None of the above
正解:D
質問 3:
Services A, B, and C reside in Service Inventory A and Services D, E, and F reside in Service Inventory B.
Service B is an authentication broker that issues WS-Trust based SAML tokens to Services A and C upon receiving security credentials from Services A and
C. Service E is an authentication broker that issues WS-Trust based SAML tokens to Services D and F upon receiving security credentials from Services D and E.
Service B uses the Service Inventory A identify store to validate the security credentials of Services A and C.
Service E uses the Service Inventory B identity store to validate the security credentials of Services D and F.
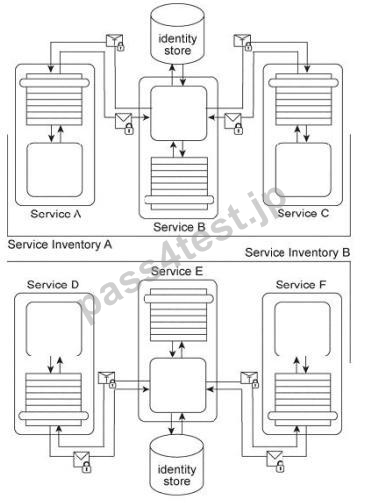
To date, the two service inventories have existed independently from each other. However, a requirement has emerged that the services in Service Inventory A need to be able to use the services in Service Inventory B, and vice versa.
How can cross-service inventory message exchanges be enabled with minimal changes to the existing service inventory architectures and without introducing new security mechanisms?
A. The Trusted Subsystem pattern is applied to encapsulate Services B and E using a central utility service that balances request and response messages exchanged between Services B and E, depending on which service inventory the messages originate from. The utility service also contains transformation logic to ensure that the SAML tokens issued by Services B and E are compatible. This guarantees that an issued SAML token can be used across Service Inventories A and B without further need for runtime conversion.
B. Because SAML tokens cannot be used across multiple security domains, authentication brokers C and E need to be replaced with one single authentication broker so that one token issuer is used for all services across both of the service inventories.
C. The current security mechanism already fulfills the requirement because SAML tokens can be used across multiple security domains. The only change required is for each authentication broker to be configured so that it issues service inventory-specific assertions for SAML tokens originating from other service inventories.
D. The individual domain service inventories need to be combined into one enterprise service inventory. The Service Perimeter Guard pattern can be applied to establish a contact point for request messages originating from outside the service inventory. Within the service inventory, services no longer need to be authenticated because they are all part of the same trust boundary.
正解:C


 919 お客様のコメント
919 お客様のコメント





Mayama -
すごく良いS90.20の問題集だと思います。暗記が勝負のところがあるので