When establishing server-side SSL authentication for an SSL connection, which one of the following sequence is used to establish a successful connection?

A. Option C
B. Option A
C. Option D
D. Option B
正解:B
質問 2:
A company wants to implement disaster recovery (DR) between a9004/9235 appliance and a 9005/7199 appliance. The company is also considering the inclusion of a DR-enabled XI52 virtual appliance in the plan. The following conditions apply: ?The source and target hardware appliances are located in geographically dispersed data centers. ?The firmware level is V5.0.0.x on the appliances, and the appliances and licenses are compatible. ?Both appliances have a different set of users that need to be merged on the restore. ?The source appliance has been initialized with disaster recovery mode and is to be securely backed up and restored on to the target appliance. Which one of the following statements is TRUE and allows the solution implementer to meet these conditions?
A. The secure backup from the 9005 physical appliance can be restored on the virtual appliance since they are both 9005 implementations.
B. Merge the contents of the source appliance with the target appliance by NOT selecting the "overwrite" option when prompted, which will merge the users on the target appliance.
C. Only the source appliance must be set to disaster recovery mode for the secure restore to be successful.
D. After the secure restore, the users that were defined on the target appliance must be manually configured or imported from a previously-exported configuration.
正解:D
質問 3:
A solution implementer has created a stylesheet as shown in the following exhibit.

Which output would be generated when the above XML is transformed by the given stylesheet?
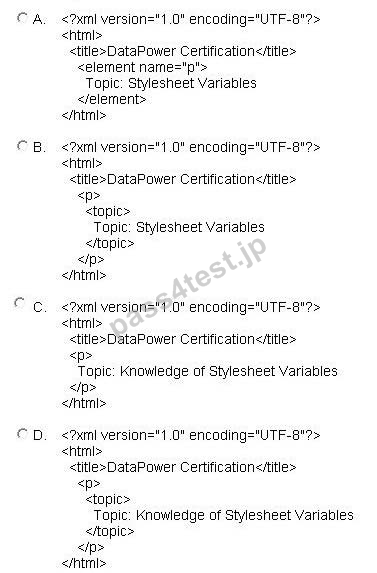
A. Option C
B. Option A
C. Option D
D. Option B
正解:A
質問 4:
A solution implementer has created a Deployment Policy to scan through configuration objects when they are imported and to remove any references to appliance specific settings such as the Ethernet addresses. Which of the following Deployment Policy settings would provide this functionality? (choose two)
A. A Filtered Configuration with a list of the objects that are to be excluded.
B. An Accepted Configuration with a list of the correct values for the properties forany named objects that will be updated during import.
C. A Modified Configuration with rules specifying Delete Configuration for the object references to be removed on import.
D. A Filtered Configuration with a list of the objects that are to be included.
E. A Rejected Configuration with a list ofthe objects that must be rejected during import.
正解:A,C
質問 5:
A financial services company (Company) is using a DataPower appliance to securely access an external service provider (Partner) that processes SOAP/HTTPS payment transactions and returns the responses to the requesting application in the Company with payment confirmations. The Partner requires that Company establish non-repudiation so that the financial services company cannot deny that the payment transaction was originated by them. The Company requires that the confirmation sent back from the Partner also requires non-repudiation. Which of the following statements is true?
A. Request Rule must Verify with crypto object containing Company public certificate and Response Rule must Sign with crypto object containing Partner private key
B. Request Rule must Sign with crypto object containing the Company private key and Response Rule must Verify with crypto object containing Partner public certificate
C. Request Rule must Sign with crypto object containing the public certificate of Partner and Response Rule must Verify with crypto object containing Company private key
D. Request Rule must Verify with crypto objectcontaining the private key of Partner and Response Rule must Sign with crypto object containing Company public certificate
正解:B
質問 6:
A solution implementer is tasked to use a DataPower appliance as an intermediary for providing Web 2.0 services. Which of the following features of Web 2.0 messages should the solution implementer be aware of when designing thesolution? (choose two)
A. Web 2.0 messages can be secured by WS-Security.
B. Web 2.0 use cases are best suited for a web service proxy service.
C. Web 2.0 message and a SOAP message cannot be processed by the same processing policy and front side handler of a DataPower Service.
D. Web 2.0 REST messages can use HTTP POST methods like SOAP messages.
E. Web 2.0 messages can arrive with an empty body.
正解:D,E


 993 お客様のコメント
993 お客様のコメント





堀江** -
ここPass4Testの出た試験対策問題集は解き方がよくわかる詳しい解説が好きです。C2180-274にみごと合格いたしました